8 minutes
How can we let the business feel like an adversary?
Background
Recently, we had a “Cyber Roadshow” at the organization I work for. Our Cyber RoadShow is an internal event where various security teams get the chance to present and educate other employees from multiple teams about various cybersecurity topics - sharing knowledge about trends, projects, tools, methodology, and more. We even bring industry leaders and business partners to share their views and ideas about other cybersecurity-related topics.
The Roadshow is carried over a few days, a few hours each day, and broadcasted over VC. Hence, all the teams worldwide can tune in and participate, and the schedule is shared in advance. I was lucky to be invited to present a session that provides an “Adversary Point of View.”
Why?
I think most of us are tired from remote and\or virtual presentations, especially after the last three years of covid. That’s why it is harder to keep people hooked to your presentations, deliver messages - on the other hand, it gives you the option to innovate.
Usually, when I present internally, people are interested in hearing about my area of responsibility (Offensive Services) and what it means, what we do, how we do it, etc. This time I was interested in doing something a little different, exciting, and, most of all - interactive. I wanted to let the audience be a part of the talk and give a whole experience instead of just hearing me talk. The other goals for the Cyber Roadshow were to have the audience learn something new, understand more about the different security programs and engage them to understand the importance of the security program and projects.
Some other key things to keep in mind when planning the session were:
- The type of the audience - the audience is a mix of different people with different skills, career focus, technical knowledge, and background. So we need something that won’t require specialized experience or prior knowledge.
- Presentation is virtual - need something that doesn’t depend on physical elements or demos that require in-person participation.
- Time is limited - the session was allocated for a 30-minute window (including Q&A), so there was no time to go too deep or to explain complicated topics
- People will be tired of “more of the same” - the session was scheduled for the 3rd day, and the audience already had many other sessions and “standard” presentations
How?
So what should I do?!
I had an idea that felt really cool! I was reminded that in the past, I saw something cool published by Tim MalcomVetter; he posted an “interactive blog” some time ago, you are welcome to check it out yourself, but the TL;DR is that it is a blog post that outlines a red team operation where the reader can choose how to advance and find out how the story evolves.
I decided I would do something similar, with a bit of different content (suited for business people and not security professionals). The storyline will be based on actual events and decision points we encounter as adversaries.
Going into the planning mode (“Fortuna Eruditis Favet”), I started thinking about the best way to achieve it. To avoid getting stuck in planning “the perfect solution” I decided to just start building the content. I’ve used a slide deck for the delivery of the entire session. The first few slides were explanations (what we are about to do and how). Then, background (what is the storyline, what I’ll do as the “Threat Master”) for removing any fear or doubts from prior requirements (like technical knowledge, hacking experience, etc.). Last was the administration (how to log into the voting platform, more on this later). Once that was done, I presented one question as an example to let people see what they need to do and how it works. From there, we moved to the actual scenario.
So before explaining the voting system, I want to describe the structure and how I’ve decided to make it interactive: The deck outlines a story that puts the audience in the shoes of a threat actor. As the “Threat Master” I am the one explaining what’s going on. Then, I read their options for each step (similar to a Dungeon Master in D&D). The way it’s presented is that the slide title contains the current situation (What you see, what you can do), and there are a few options on the slide. After explaining each option, a voting system (3rd party integration) starts for 15 seconds (that felt like a sweet spot for time to vote). The audience votes on which way to go forward after the timer is out, and the voting results are updated on the slide itself (a very cool feature by the 3rd party). Finally, I’ll click an option of the most voted choice. Here’s an example of such slide to help you visualize:
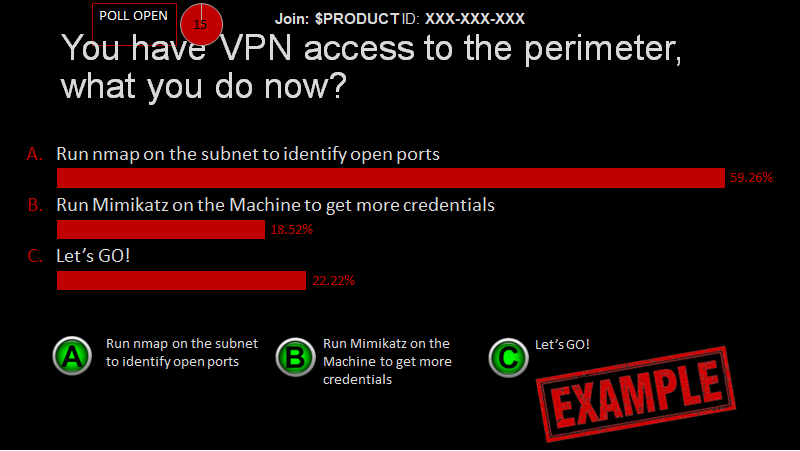
It is important to note that when narrating the story, you need to remember a few things:
- You should explain any term and what it means; most of your audience never ran “Mimikatz”
- You should describe the situation like a story, not “you got creds; let’s hack something else”
- You should not describe what they (should) think, know, understand or prefer - the main idea of the session is to put them in the adversary’s shoes. Provide them with the ability to understand how it feels when attacking something and when you need to make operational decisions.
- Try to add some additional information that can teach them and help them get into that mindset, and keep everything realistic but still dramatic for the engagement. You can even let them use the chat (or unmute) to discuss the next step to simulate what really happens in the teams
So, to recap - we have a few slides for logistics, then an example slide, and then each step slide has the current situation and a few options to choose from. Of those options, some were “mistakes” and some were “correct”, I didn’t use a fixed ratio. A “mistake” option would lead to a slide that explains why they were caught, by which system and which team, and how (if relevant) - this helps share the benefits and importance of various used security tools and teams. On each one of the “caught” slides, there was a “reset” button that brings you back to the original slide, so we can go for the 2nd most voted option, and so forth until the “correct” slide takes you to the next “situation” slide and you move forward Example “caught” slide: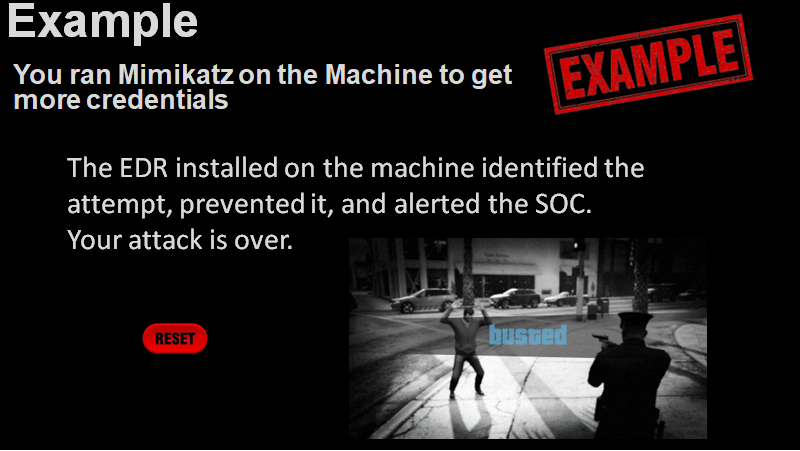
In some cases, I’ve made a situation where all the options “were right” just to break any pattern and increase the chances everything will feel realistic and not too “gamed”. For me, I’ve prepared a total of 17 “scenario” slides, most of them had three possible decisions, and even though we didn’t get to see all of the results, it fitted perfectly for a 30-35 minute window, including having the audience set up their participation, some discussions, explanations of terms or situations, and even some discussion in the end about reality, defense concepts, and lastly, the way I (and probably others) look at defense strategy (will be discussed in a separate post - Defense strategy, how I see it)
To summarize, I had a few goals with my session - it started with goals related to educating about different technologies used and a different experience for the audience. It ended with the will to give others a chance to experience how it feels to be in adversaries' shoes when they need to make operational decisions. I heard people saying that hacking is easy, and I somewhat agree with it. Because most of the attacks we see are people pointing public tools at a system\vuln and exploiting it, we can argue what is “hacking” and then argue if it’s easy. In this case, hacking is easy; However, the hard part is when you need to make decisions during your operation. Who to target? Which file to steal? Is this user a deception? to start with a scan or to go after the CVE? These questions are crucial during an assessment. And the reason for it is simple - are you familiar with the saying, “Attackers need one win to get in, defenders need 100% wins to prevent it”? I think it’s true. But, I claim this paradigm changes 180 degrees once the adversary is inside - then they operate in the defenders' field, and they need 100% success to avoid getting caught. The defenders need 1 win to pick them up and cut their access (potentially preventing them from achieving their operational objectives).
I believe this session went well - and based on the feedback I’ve received, people had fun participating, had fun having a different type of session, and most importantly, learned new things:
- What are the operational considerations of adversaries?
- What are some points where we can slow them down?
- How does it feel when you need to make quick decisions during your attack? And I call my peers in offensive security to make something similar in their organizations and offer improvements. I believe that providing other people in the business access to our tradecraft from the inside, without the barriers of technical knowledge, will assist them in understanding the value of what we offer. It will provide them a better understanding of the threat actors they are facing and the importance of various security improvements.

P.S - execution tips
One important thing I’m glad I’ve considered is to have content to speak about when you are sharing the slide with the voting details - because, in this slide, people need to open their phone or browser to go to a URL and use a code (or scan a QR code). Also, it can take some time to gather everyone (or most of them) so having something to talk about while everyone is connecting helps you engage more people from the audience.
Not how many, but where.
Roei Sherman